Less than a year after its predecessor, CryptoWall 3.0 (which inflicted an estimated $325 million in damages in the US alone), the most recent version of the world’s worst ransomware has surfaced, CryptoWall 4.0. While the end result for the attackers remains the same, to extort money from victims whose files have been encrypted and held for ransom, the malware itself has gotten a major facelift.
What’s new about CryptoWall 4.0
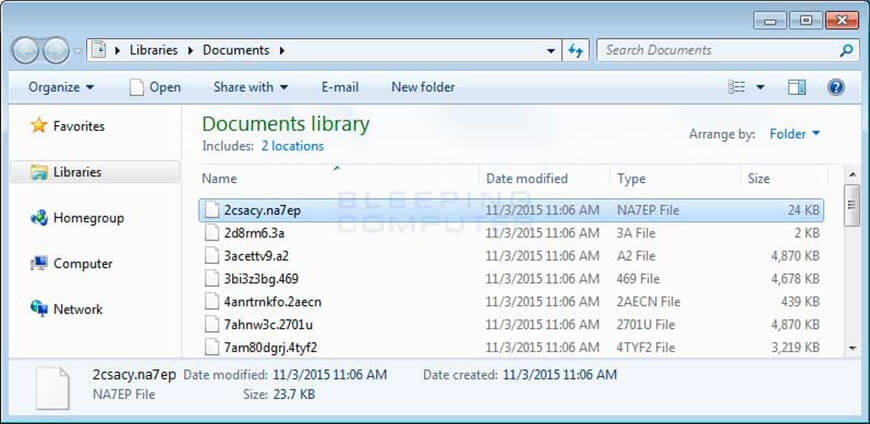
Like the previous version, this one is being transmitted through emails with a “resume.zip” extension but unlike the previous version, researchers note the encryption of filenames along with the encrypted files and data to be the biggest and most significant change in CryptoWall 4.0 (see image below).
“This is a first,” according to Nathan Scott, an independent researcher who examined the code with Security Colleagues at Bleeping Computer. “I’m surprised more don’t do it; this makes it significantly harder to recover files except for paying the ransom. If you try to do a forensic data recovery, the files show up with these weird names and the user doesn’t know what file is what,” Scott said. “The only way to regain your data is a complete backup. If you don’t backup, the only way to get the data back is to pay the ransom.”
System Restore Points are also erased in this revamped version, taking away the option of returning to a previously saved state. Also, “CryptoWall 4.0 still includes advanced malware dropper mechanisms to avoid antivirus detection, but this new version possesses vastly improved communication capabilities,” according to Andra Zaharia of Denmark-based Heimdal Security. “It includes a modified protocol that enables it to avoid being detected, even by second generation enterprise firewall solutions. This lowers detection rates significantly compared to the already successful CryptoWall 3.0 attacks,” said Zaharia.
What should you do to mitigate your chance of a CryptoWall 4.0 infection?
There are many ways you can help to prevent a Cryptoware infection and proactive measures to put in place that will lessen the impact an attack can have. Some of them are:
- Back up your data constantly and frequently, ensuring that your backup systems are working properly and you have tested the restore functionality
- Do not open spam emails or emails sent by unknown senders and do not download or open any attachments within those emails
- Use products that can detect and block recent Cryptoware variants and ensure that your anti-virus and/or anti-malware applications are up to date
- Keep your system up to date and always install the latest updates available

Here at Dean Dorton Technology, we know that no solution is 100% guaranteed to prevent and block all ransomware from infecting your companies’ network. For that reason, it is vitally important to ensure you have a complete backup and disaster recovery solution in place. If you would like to learn more about the solutions we can provide, please contact John Miller at (859) 425-7701 or jomiller@ddaftech.com to set up a consultation today.