Cybersecurity Scorecard Assessment
Our approach
Dean Dorton has created a proprietary process that helps measure key elements of your security program, and focuses on providing actionable recommendations to improve your organization’s cyber security posture. Get your personalized scorecard today!
- FAST – Our assessment process is designed to move faster than the threats that increase risks to your business. Once we begin testing, you will have all the results available within 48 hours. Testing processes are conducted over a single business day.
- SECURE – The protection of your business is OUR business. This value extends from our testing methodology, process, and handling of data collected from your environment. We use industry best-practice encryption for file transfers, multi-factor authentication, and data retention policies to reduce risks.
- AFFORDABLE – The old adage of only being able to pick two from “you can have it fast, affordable, or good” no longer applies. We used our years of experience conducting technical security assessments to develop a methodology that provides meaningful results, actionable recommendations, and a concise and clear posture of the environment all at a more than reasonable cost (in some cases, 10-20% of what you would pay traditional firms).
Over 43% of malware related cyber breaches occurred in small businesses
According to recent research, over 43% of malware related cyber breaches occurred in small businesses, with only 14% prepared to defend themselves. Most small businesses lack the budget or resources to create a cybersecurity posture strong enough to reduce cyber risk. This often makes them easy targets for opportunistic malware cyber attacks distributed by organized cyber crime syndicates. This leaves at-risk small businesses with many questions.
How much security is enough?
The more personal data that flows through your network, the more safeguards necessary to keep it secure. Organizations in certain industries — like finance and healthcare — are more vulnerable to cyber threats due to the nature of their business. With the current ever-increasing sophistication and frequency of cyber attacks these days, all businesses need to have mitigation measures in place to reduce risk and better protect their networks and customers’ sensitive information.
How do we know what we are doing is enough?
Any amount of effort to mitigate cyber risk is better than no effort at all. That said, a strong cybersecurity posture built to minimize damages when they occur helps businesses comply with increased regulations, save costs, and safeguard reputations. At Dean Dorton, we offer an independent cybersecurity audit as the first step toward identifying fixable weaknesses and the development of personalized cyber risk protection strategies.
What does a small business cybersecurity program look like?
A robust cybersecurity program includes layers of tools, technologies, risk management approaches, and best practices (like cybersecurity training for your whole organization). With these strategic measures in place, you’ll be able to increase real-time visibility across your network and devices while improving your team’s ability to react in the event of a breach.
How do we make cybersecurity measurable, actionable, and attainable?
Remote work is more widespread now than ever. When the shift first occurred, most businesses didn’t have the time or resources to properly prepare their networks before connecting employees in work-from-home environments. Coupled with the proliferation of the Internet of Things (IoT), the ever-changing digital landscape has significantly increased overall risk of cyber attacks. More connected devices using more different software services across dozens of different locations leads to a lot of potential weak points within an organization. The need has never been greater for small businesses to insulate themselves from cyber risk by adopting advanced cybersecurity precautions.
OUR DESIGN
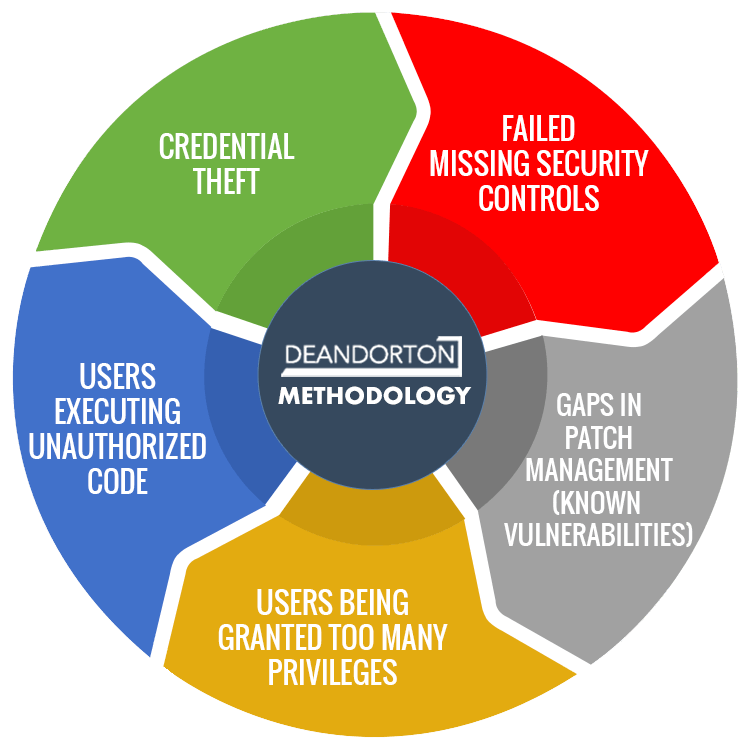
With years of experience conducting technical security assessments and penetration tests, we’ve come to the following conclusion: threat actors use the same tactics in the vast majority of breaches.
Not all small businesses are the same, but many of the cyber risks they face are. That’s why we designed our methodology to identify these risks, assess their status using easy-to-follow metrics, and help implement subsequent protections.
OUR SCOPE
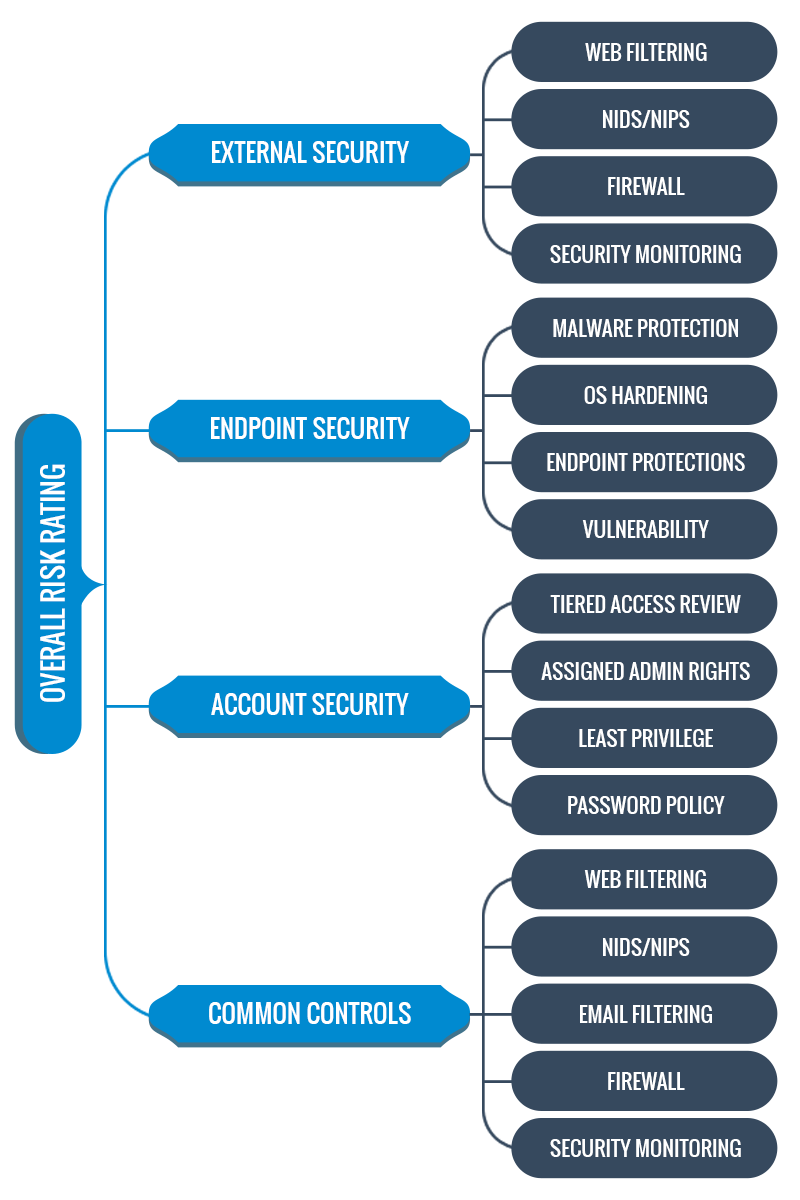
We looked at the most common tactics, issues commonly exploited, and the controls organizations need to implement to mitigate these tactics to design our scope.
We designed our scope by analyzing which cybersecurity tactics worked best, which issues were most commonly exploited, and which controls were most needed to secure at-risk organizations.
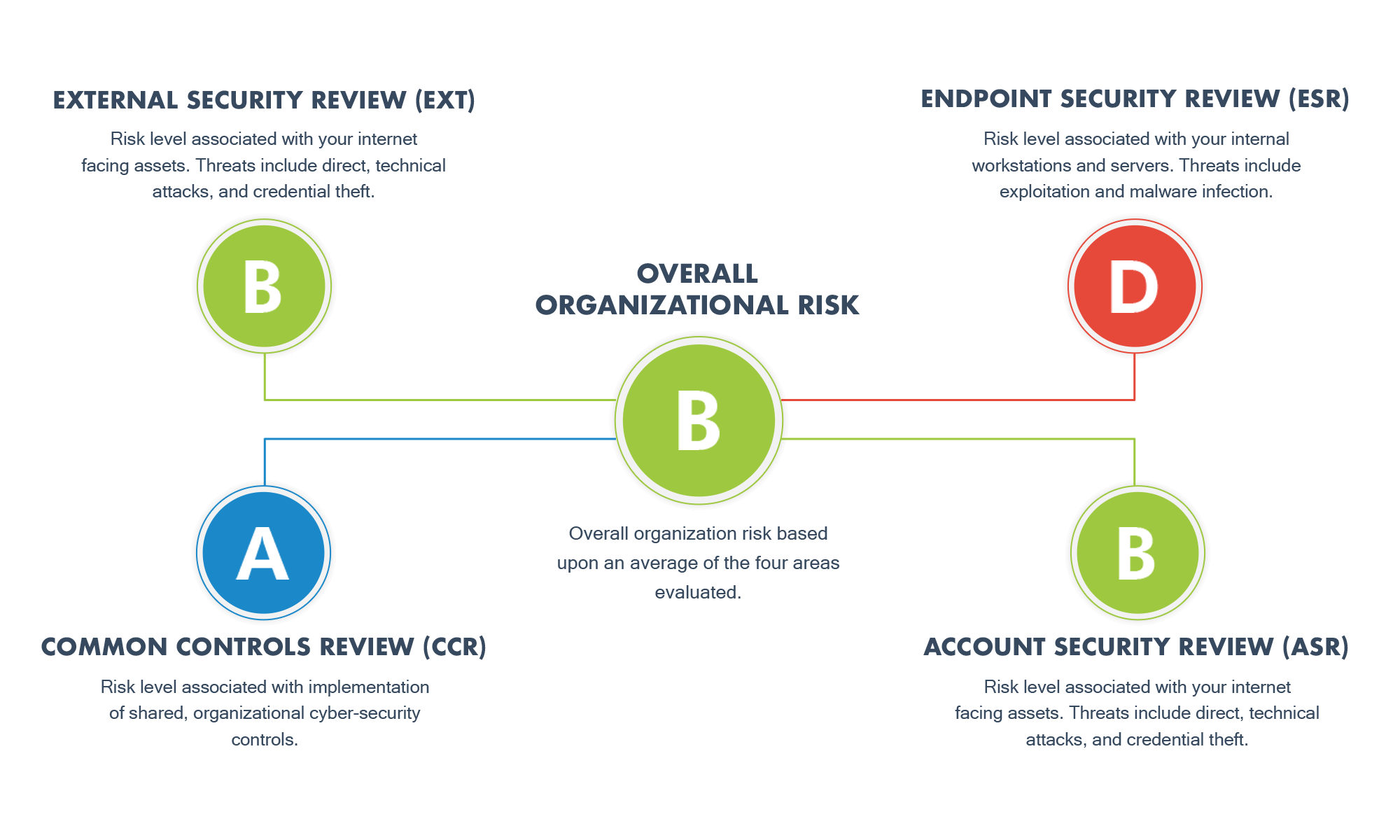
The result is an in-depth, detailed review of four core security domains, comprising 17 unique control areas.
Each control area is scored individually. Control area scores are combined to obtain a cyber risk score for each domain, which is then averaged into an overall risk score for the organization based upon a common grade scale.
METRICS THAT MATTER
What metrics do you need? How do I measure these?
These are questions that Dean Dorton’s Cybersecurity Scorecard Assessment provides the answers for.
We have developed a grading system that measures the accumulated risk based upon identified security issues or ineffective controls. These risk ratings are combined to provide both domain-level and overall organizational risk.
To further communicate what these mean, we tie the risk levels back to a threat actor scale (courtesy of the Verizon Data Breach Report) to help you understand the types of threat actors your current posture protects against, and who you are still vulnerable to.
EXECUTIVE PRESENTATION
The executive presentation provides a high level review of the results of each domain, and visualizations of key data collected (such as attack surface maps).
SECURITY ASSESSMENT REPORT
The security assessment report contains an analyst overview of the collected data, including detailed analysis of each control area. The report also includes a detailed action item list to hand off to your IT team our outsourced managed service provider.
EXCEL REPORT
The excel report includes several tabs (one for each domain) and detailed action items (down to the host level) of issues that contribute to risk observed for the environment. System Administrators can use these details to remediate specific issues that will increase the security posture of the organization, and improve the overall risk score.
SCORECARD EXECUTIVE DASHBOARD